Both rely on a peer-to-peer routing structure and layered encryption to make browsing private and anonymous. Unlike Tor, however, it cannot be used to access the public internet. It can only be used to access hidden services specific to the I2P network. I2P cannot be used to access .onion sites because it is a completely separate network from Tor.
How Much Does It Cost To Use Tor Browser?
That’s why dark web scans are important so you know if your personal information is compromised. From journalists and civil society organizations to regular individuals with online privacy concerns, Tor Browser users are a diverse group. But criminals also take advantage of Tor’s anonymity to carry out illegal activities both on and off the dark web.
- More curated and potentially safer directories include Tor Taxi and Dark Fail, which often attempt to vet the links they provide.
- This encrypted data is then randomly bounced through a series of relays, operated by volunteers across the globe.
- Others were casual users—people buying fake IDs, stolen credit card numbers, or drugs.
- He travels between the UAE, Turkey, Russia, and the CIS as a digital nomad.
- Anything you need to do that has to be off the books to some extent, for noble or ignoble reasons, can be done on the dark web.
For over 40 years, PCMag has been a trusted authority on technology, delivering independent, labs-based reviews of the latest products and services. With expert analysis and practical solutions across consumer electronics, software, security, and more, PCMag helps consumers make informed buying decisions and get the most from their tech. From in-depth reviews to the latest news and how-to guides, PCMag is the go-to source for staying ahead in the digital world.
How To Stay Safe While Using Tor Browser
Most top VPNs have paid subscriptions, but there are also a few providers that have good free plans that let you test their services. And unlike the Tor browser that only secures the traffic that passes through it, a VPN secures all of your device’s web traffic. You can access many other sites via the Tor browser, and your requests will be routed through multiple servers to avoid monitoring. However, some websites consider Tor traffic suspicious and make users jump through several hoops, including CAPTCHAs.
Can I Be Traced, Tracked, Or Hacked If I Use Tor?
Other options include Ahmia and NotEvil, which focus on listing .onion links. Hence, you never know when a popular .onion site is going to vanish, or even die. Though it’s still helpful, a static list isn’t enough (we try to keep our own, the one above, up-to-date, though). The best thing is to actually understand how to find the fresh, new links. Blockchain.info (now Blockchain.com) is a popular cryptocurrency wallet and blockchain explorer service (one of the first sites to launch on the dark web).
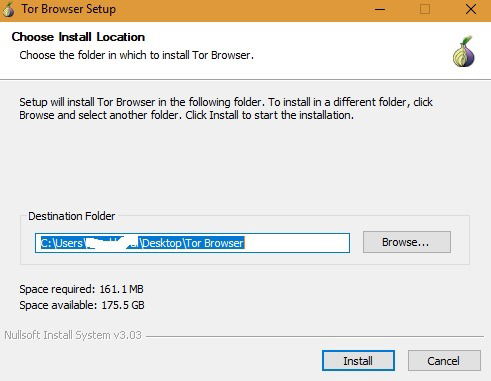
Many if not most computer users have accepted the Faustian bargain that cost them their privacy in exchange for a world of entertainment and information. But if you want to claw back some of your data from the brokers and miners, downloading and using Tor is a free and easy way to do it. There is only one official download site for the Tor browser, and that is torproject.org. Builds of the browser are available for Windows, MacOS, Android and Linux systems. The dark web is full of unknown and potentially dangerous content.
Hacking And Cybercrime Services
Activists and government critics prefer to remain anonymous, fearing repercussions if their identities are revealed. Besides, victims of crime may want to hide their identities from their perpetrators. Nonetheless, if whatever you do is deemed illegal in your country, you can get into trouble. Therefore, the legality of the dark web will mainly depend on how you use it. You can quickly get into trouble for acting illegally, such as infringing on other people’s safety and freedom.
Commercial Services
A reliable, fast, and user-friendly VPN service offering lots of customizable options for privacy geeks. Most likely, the native account on your device has full admin permissions by default. Many malware take advantage of this vulnerability to launch an attack.
Dark Web Tools And Services

Basically, you just need to set it up to use a SOCKS5 proxy on port 9050 (which is where Tor usually listens), and you’re ready to browse more anonymously. Join millions of users who trust ForestVPN for privacy and unrestricted internet access. The dark web can be dangerous due to the presence of scams, cybercriminals, and malware. Users should exercise caution and follow safety practices to minimize risks. For many of us, the dark web represents an enigmatic corner of the internet, often shrouded in myth and misunderstanding. Yet, beneath its shadowy veneer, it offers both legitimate and illicit opportunities, making it a topic of fascination and concern.
A piece of tape over your webcam essentially prevents any possible remote activation by malware. Assume that everyone and every site is trying to take advantage of you. Avoid giving up real information, don’t log into your personal accounts, and don’t engage in conversations that could identify you. Similar to Firefox and Waterfox above, Brave is not a dedicated dark web browser.

Consequently, the Dark Web as we recognize it today started to take shape, with websites and services specifically designed to operate within this hidden network. The history of the Dark Web is intricately tied to the development of internet technology and the ongoing pursuit of online anonymity. The concept of an encrypted, hidden layer of the internet began taking shape in the 1990s. The U.S. Naval Research Laboratory developed the precursor to the Tor (The Onion Router) project during this period as a means to protect government communications. Other search engines like Haystak boast millions of indexed pages and advanced filtering options.
If You’re Still Nesting IFs In Excel, You’re Doing It The Hard Way
In opennet mode, the network will automatically assign you to other users on Freenet’s network. As I mentioned previously, the dark web is quite popular with journalists, political bloggers and news publishers, and others who run the risk of imprisonment in countries like Iran and others. Supreme Court will allow the FBI to search and seize any computer that’s using the Tor browser or VPN.
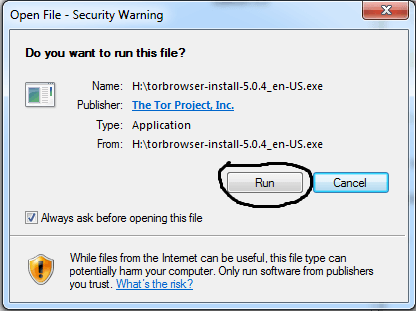
Just remember, besides using one of these browsers, be sure to pair it with a good VPN service too. Navigate to the Tor Project’s Download page, select Download for Windows, and then double-click the downloaded .exe file to install the browser. We test each product thoroughly and give high marks to only the very best. We are independently owned and the opinions expressed here are our own.
Launch the Tor Browser from your desktop or Start menu, then click Connect on the welcome screen to establish a secure connection to the Tor network. Install Norton VPN to help you access content and safeguard the data you share. Which dark web browser did you use to visit sites on the dark web? Beyond DuckDuckGo, other options have failed to keep up with the evolving landscape. Though these browsers are effective at serving up dark web search results, the experience is reminiscent of browsing the web in the late 1990s. Keep in mind that in some regions like China and Russia, it’s illegal to use anonymizers.
Some users also share links on encrypted apps like Telegram or Keybase that you can check. RiseUp is a top dark web website that offers secure email services and a chat option. It was created in 1999 as a secure communication platform for people and groups working on liberatory social change. The platform is protected from government interference and malicious attacks to protect the user. In addition, it ensures that no record of communication is stored.
You can look for information on /r/deepweb, /r/TOR, or /r/onions, of which the latter is useful to find hidden wikis and more. Many of these Reddits have rules prohibiting linking to illegal sites and services, so you likely won’t find anything illegal there. The core principle of the Tor network was first developed by U.S. Naval Research Laboratory mathematicians and computer scientists in the mid-1990s.
Whonix combines the Tor network, a Kicksecure Hardened core, and the security by isolation principle for a comprehensive privacy solution. Although the dark web is rumored to be hard to access, the Tor Browser is just a quick install away. With Tor installed on your PC or mobile phone, you’ll be able to browse active onion websites and protect your online privacy and anonymity. Social networks, such as Facebook, have created dark web versions of their sites to address privacy problems related to their surface web versions. ExpressVPN had created a .onion version of its website to allow greater privacy and anonymity for Tor browser users.



