However, by staying informed and adopting proactive security practices, you can significantly mitigate these risks. Financial literacy, regular account monitoring, secure online behaviors, and utilizing advanced protection methods such as two-factor authentication and virtual cards are essential strategies. Moreover, being alert to signs of card compromise and knowing how to respond swiftly if your data is stolen can drastically limit potential damage. Safeguarding your credit card data from theft involves proactive measures and timely responses. By following clear, practical guidelines, you can significantly reduce the risk of becoming a victim of carding or related fraud. Artificial intelligence (AI) has become indispensable in the fight against carding.
Credit Card Fraud On The Dark Web
Social Security numbers and other national ID numbers are for sale on the dark web but aren’t particularly useful to cybercriminals on their own. Alex Herrick is a seasoned web designer and digital strategist with over a decade of experience in the industry. Passionate about blending creativity with functionality, Alex specializes in crafting visually compelling websites that drive results. His expertise spans across web design, SEO, and digital marketing, making him a key contributor to Web Design Booth’s mission of empowering digital creators. The threat actor behind the AllWorld Cards marketplace has a clear goal in mind. They are actively promoting the platform on Dark Web hacking-related platforms since late May 2021.
Risks And Challenges
- Another method employed is card skimming, where criminals install hidden devices on legitimate payment terminals or ATMs to capture card details for later use.
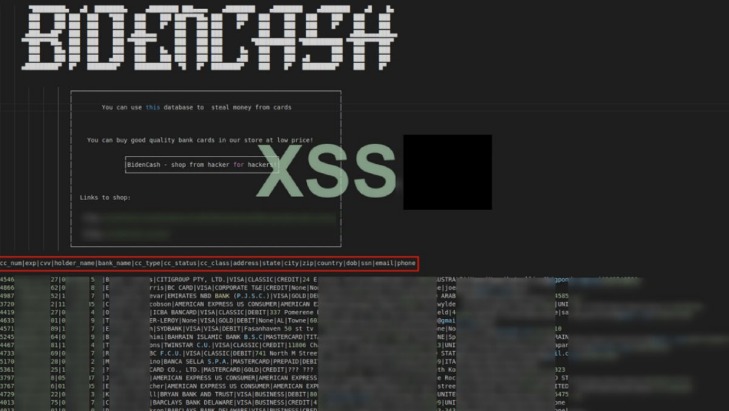
- The first leak offered only the information contained in magnetic stripes of compromised cards, while the latest sale includes fullz – card number, expiration date, CVV/CVC, cardholder name, and extra personal info.
- Due to limited data on credit cards from other countries, we were unable to adequately compare prices for credit cards from different places.
- A 2019 data leak of another shop, BriansClub — which appears to have been by a competitor, according to Threatpost —shows how pervasive this trend has become.
- Other sellers offer discounts for buying multiple cards, while the cheapest card — with between US$700 and US$1,000 on it — can cost as little as US$80.
And they are also supposedly safe to use because they have already been purchased using another credit card before they are sold to you. Some sellers even say that the cards can’t be tracked because of that same reason. Stolen credit card numbers are often used for online shopping sprees or to make in-store purchases through digital wallets. These transactions can happen across different countries, making them harder to trace. If your card is linked to auto-pay services or has a high spending limit, the damage can escalate quickly—often before your bank even flags it as suspicious. If you’ve ever wondered where your stolen credit card turns up, a cybersecurity firm is offering hard proof.
In brute-forcing, a computer tries to guess your password, testing a series of numbers until it gets it right, possibly in as few as six seconds. A computer is able to “make thousands of guesses a second,” Briedis said. “After all, criminals don’t target specific individuals or specific cards. It’s all about guessing any viable card details that work to sell.” These aren’t just random forums, they’re organized platforms where stolen card data gets packaged and sold as “fullz” (full card details including CVV) or “dumps” (raw magnetic stripe data). Additionally, fraudulent charges can lead to overdraft fees, late payment penalties, and damage to credit scores. These financial losses can have a lasting impact on victims’ financial stability and may require extensive efforts to resolve the issue and regain control over their finances.
Contact Your Bank Or Credit Card Issuer
- Flare monitors the clear and dark web as well as illicit Telegram channels for high-risk external threats to your organization.
- If questionable data is detected, understanding next steps is critical to minimizing risks to your brand, employees, and customers.
- That merchant specifically mentioned that using a stolen card on a store that uses Verified by Visa (VBV) will likely void the card.
- Even if you report the fraudulent activity quickly and limit your losses, you may still face the issue of bounced checks or being late on payments, Krebs says.
- Credit card fraud on the dark web operates quite differently from what many people imagine.
It is one of the most active and up to date markets and always provides new and updated malware and data. Beginning in September 2021, Abacus Market has established itself as one of the leading dark web marketplaces. After AlphaBay closed, Abacus Market took its place as the world’s largest underground darknet marketplaces. Abacus Market quickly rose to prominence by attracting former AlphaBay users and providing a comprehensive platform for a wide range of illicit activities. Our team searched the dark web and put together a list of the most active dark web marketplaces in order to assist you in monitoring illegal trade of products, cybercrime activity, and dark web trends in the dark web space. Based on our observations from analysis on dark web data using Lunar, we’ve identified the top 7 marketplaces on the dark web in 2025.
They’ve essentially created a parallel economy with its own reputation systems, escrow services, and even customer support channels. Credit card fraud on the dark web operates quite differently from what many people imagine. Additionally, it’s crucial to stay informed about the dark web’s evolving tactics and trends to mitigate risks effectively. One of the largest known underground shops, Joker’s Stash, generated more than $1 billion before getting shut down in February, according to Gemini Advisory.
In 2021, around 96 million credit cards were sold on the dark web, as per an annual report from cybersecurity firm Gemini Advisory which tracks such transactions on the dark web. These include 36 million Card Present (CP) records, where the records are stolen from physical stores from point-of-sale machines. Rest 60 million were Card Not Present (CNP) records, where the details are stolen from the checkout pages of websites where card information is entered purchases or payments. Detecting and preventing dark web credit card fraud can be difficult since the dark web is, by nature, hidden. By using specialized tools cybersecurity professionals can track these illegal activities and alert financial institutions of potential threats. Purchasing and using stolen credit cards is treated as a serious criminal offense with substantial legal consequences, both in the United States and across the European Union.
Why Are They Sold?
“These days, Dark Web sites compete on the quality of their security and customer service,” Ruffio states. “So, it’s no surprise that they now use traditional marketing tactics, too. Discounts (Buy 2 cloned credit cards, get one free), coupons, and product reviews are becoming common sights on the most competitive sites.” Dark web credit cards refer to stolen credit card information that is bought and sold on the dark web.

Stolen Credit Cards For Cheap, And Credentials On Sale: Darknet Pricing Revealed
While financial institutions use advanced AI systems to detect and prevent fraud, criminals are simultaneously harnessing similar technologies to bypass security measures. Cybercriminals are likely to adopt AI-driven bots that rapidly test stolen card data, create sophisticated phishing attacks, and evade detection algorithms by mimicking legitimate user behavior. Immediately upon completing the transaction, buyers receive access to the purchased data. This information is usually delivered electronically within the marketplace, either displayed directly or provided as encrypted files accessible via secure downloads. From here, buyers proceed to utilize this stolen information to commit fraud—typically by making unauthorized online purchases, creating counterfeit physical credit cards, or initiating financial transfers.
How Threat Actors Obtain And Trade Credit Card Data
Finally, criminals “cash out,” converting assets like resold electronics, gift cards, or cryptocurrencies into cash. Methods include withdrawing cryptocurrency via exchanges or Bitcoin ATMs, transferring funds through money-mule bank accounts, or receiving payment through online payment systems (such as PayPal or peer-to-peer platforms). This final stage completes the monetization cycle, allowing criminals to realize profits from stolen card information. Before making a purchase, experienced buyers often validate the authenticity and usability of the offered credit card data using online tools known as card checkers.

The Real Deal On Legit CC Vendors: No Bullshit, Just Results
It equips cybercriminals to access the credit card details stored on the system after the breach. Involving yourself in the purchasing or selling of stolen credit cards is a risky business. It’s also pertinent to note that stolen credit cards have various types based on their value and risk. Dumps have the most negligible value and risk, whereas Fullz cards have the most value and risk, and CVV2s include the three-digit security codes found at the back of the credit cards. It is understood that the data included such highly sensitive information as the primary account number of the credit cards concerned, along with expiration dates and the card verification value, CVV2, security code. But that’s not all; there are also cardholder details such as their full name, address, date of birth and telephone number as well as email address.

Fullz that come with a driver’s license number, bank account statement, or utility bill will be worth more than those without, for example. These groups often originate from leaked credit card credentials, which have become a common phenomenon, particularly in the past months. Such type of data is likely to have been compromised online, making it a red flag for would-be fraudsters. Vendors sell additional information about the cardholder, known as “fullz”, which includes the cardholder’s social security number, street address, birth date, and more.
However, this raises the question of how likely credit card theft can happen, by population. Immediately, looking at the previous chart, we can notice Quebec at 9.8% of total cards found, even though Quebec represents a lot more than 9.8% of the total Canadian population. Indeed, Quebec accounts for about 22.46% of the total Canadian population. The following graph represents the amount of stolen credit cards by province, per 100,000 population. Our researchers found one ad asking $5,000 for access to a corporate network, while another was priced at $2,500 for VPN credentials purportedly to a Korean company with an estimated $7 billion in revenue. The common verification flow has the person who bought the stolen bank needing to confirm identity to the bank.
Card checkers quickly verify whether a card remains active, ensuring it hasn’t already been blocked by banks or previously flagged for suspicious activity. Globally, financial institutions and businesses spend billions more each year attempting to prevent, detect, and recover from fraudulent transactions. Major breaches, such as those affecting large retail companies and financial institutions, often involve tens of millions of compromised credit card records, underscoring the vast scale and persistent threat posed by carding. This is how the site admins encourage users to post their stolen credit card details on their site first.



