Google’s purpose is to show the most relevant information to all of its users quickly and easily. That means that Google wants to minimize the amount of time users spend searching for certain queries. Did you know that Google only shows you a glimpse of all the websites that actually exist? The last time I checked, it’s estimated that the entire web is roughly 500 times larger than what Google returns in Google Search. In an emailed statement sent to Digital Trends, comments from VPNOverview’s cybersecurity analyst, David Jansen, shed a little light on why VPNOverview researched all this in the first place. Cyber intrusions include attacks against computer hardware and software such as spear phishing; malware; password attacks; and SEO attacks.
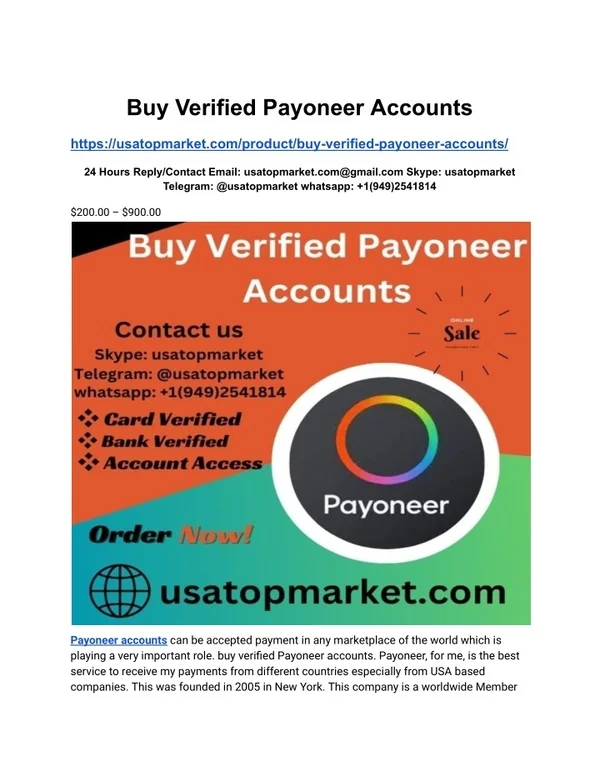
Best Free VPNs For The Dark Web In 2025: Secure & Fast
As you are now familiar with the three different sections within the entire world wide web, let’s take a closer look at how you can access the dark web anonymously. Especially for these people, the dark web is the perfect platform to communicate and publish information without having to worry about imprisonment or any other form of retribution. People in these countries potentially face political imprisonment, and freedom of speech is not absolute, such as in Iran, where users who express opposition to the mullahs running the country are harassed and/or jailed. For example, you can only find your Facebook friends, photos, and other information by logging into your Facebook account and finding the information there. The majority of the web is called the “deep web” (often referred to as the “invisible” or “hidden” web). The deep web is basically all the content that you can’t find using Google or Yahoo search.
Microsoft Warns About New Variant Of XCSSET Malware On MacOS
- With the growing threat from cybercriminals who sell stolen credit card information on the deep web and dark web, businesses need to stay ahead of the game.
- It exists on encrypted networks, such as Tor (The Onion Router), which offer users anonymity and protection from surveillance.
- But while you can’t undo a data breach, you can take control of what happens next.
- There’s also a search bar that you can use to search for any particular product or vendor.
- Bank statements can help threat actors simulate a victim’s established financial behavior, before committing actual theft.
- The dark web on the other hand is a subset of the deep web that is intentionally hidden and requires a browser like Tor to access it since many of the sites on the dark web use .onion web addresses..
– Read feedback from experienced Dark Web users or trusted individuals who have had successful transactions with the vendor. Next, we will explore how to navigate the Dark Web and find reliable vendors to minimize these risks and protect against potential pitfalls. Unlike the surface web we use regularly, which comprises websites accessible through standard web browsers, the Dark Web is a collection of hidden websites that can only be reached by using special software.
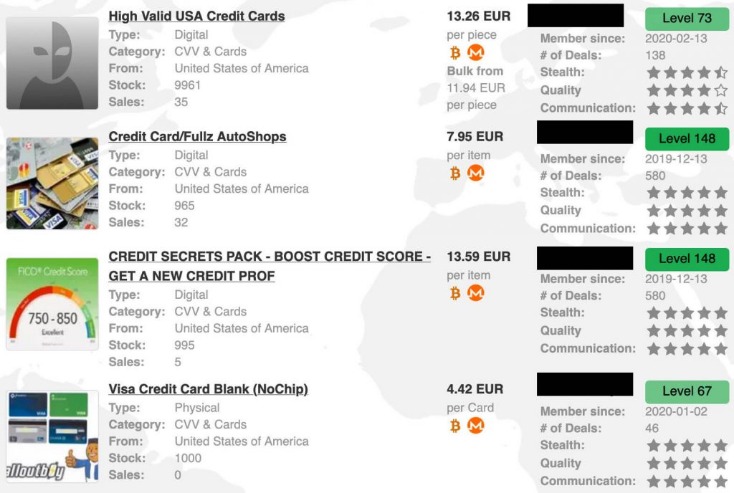
Which Type Of Credit Card Is Worth The Most On The Dark Web?
At the lowest price point are your run-of-the-mill social security numbers, birthdates, and credit card numbers, some of which even get shared for free. However, if hacked credit card digits are “fresh” (e.g.., haven’t been reported stolen), they might go for closer to $5. Over 3 million Americans each year lose money as a result of identity theft. The victims might be appalled to learn that, in some cases, their stolen data sold for the cup of Starbucks coffee—and not even the fancy kind with a double pump of vanilla. These high levels of anonymity increase the opportunity for the “bad guys” to sell drugs, stolen IDs, credit cards, weapons, and many more compromised products or information.
Top 7 Dark Web Marketplaces
Mega Market is a new yet popular shop on the dark web that reached a skyrocketing reputation after the closure of the Hydra market. It allows you to buy and sell a wide range of products and services with a good user experience. Awazon Market is a top-tier dark web marketplace with claims to revolutionize secure anonymous commerce.
Unusual Access – Reconnaissance Agent
Screenshot of listings for streaming account credentials on Nemesis darknet market. Although some of these markets prohibit certain extreme content such as violence or exploitation, most operate with very few rules beyond ensuring the security and anonymity of their users. Some fake sellers take your crypto and never ship what you ordered, or phishing sites that look like real marketplaces but steal your login info. And then there’s malware—click the wrong link or download the wrong file, and your device could get infected. Some are looking for illegal stuff they can’t buy elsewhere, like drugs or counterfeit documents. Despite growing crackdowns from law enforcement agencies, the dark web remains a hotbed of criminal activity, offering everything from drugs to stolen data.
See How Polymer Can Protect Your Organization
The most recent example is the shutdown of the oldest marketplace Hydra Market in 2022 which took a combined effort of the FBI and the German authorities. The darknet markets keep on popping even when the authorities keep getting hard on them. While there are several darknet markets, each features unique characteristics tailored to various user needs. Fake online casinos and social networks are common methods for distributing malware.
The site has a unique news section, where the admin updates the buyers about new leaks and dumps, the source of the dumps, structural site updates and more. “There are likely only a handful of major credit card data farmers doing the majority of the data theft,” Armor says. It reveals the extent to which streaming and VPN account details dominate the illicit trade in personal data on the darknet markets. This article summarizes our main findings, shares details of how hacked accounts sold on the dark web are most commonly used in fraud and shows how consumers can protect themselves from identity theft. You’re probably wondering how things like a PayPal account login or credit card details end up on the dark web.
For instance, cybercriminals can buy credit card details with a $5,000 balance for just $110. This threat actor charges 50% commission on the amount of funds laundered via financial institutions based in UAE. Besides payment data, threat actors are also monetizing stolen Personal Identifiable Information (PII). One reputable STYX Marketplace vendor focused on stolen PII is the “Fraud Store”. The bypass of banks’s existing customer authentication and fraud-prevention solutions requires special attention, which Resecurity will address in a separate research publication.
Abacus Market appeared on the scene in 2021 and quickly became one of the heavyweights among English-speaking markets on the dark web. The categories are well organized, ranging from drugs and fraud to digital products, guides, and malware.What really sets it apart is its focus on security and usability. It supports PGP encryption, two-factor authentication (2FA), alerts against fake sites (antiphishing), and a verification system for sellers. Its interface is easy to navigate, and it has a reliable escrow system, as well as allowing payments with Bitcoin and Monero. All of this has made it one of the most reliable markets still active in 2025. The following table shows the online payment platforms whose hacked account credentials were most frequently listed for sale on the darknet markets.
Flights don’t come cheap, so using stolen information to book a flight has a very high chance of alerting the bank. Be careful with your airline accounts or a hacker may get a free holiday from you. Uaware reported that British Airways accounts sell for £31.94, a 375 percent increase between 2018 and 2019. LogDog reported that eHarmony accounts sell for around $10, which made them the second-most expensive account in LogDog’s report. If you want to know how hackers use these accounts, be sure to read about the ways scammers can exploit your email address. The researchers said that the reason for the large amount of account information on the dark web is that people use low-strength passwords, which are easily cracked by brute force tools.
How Cybercriminals Use The Dark Web To Sell Stolen Data
None of the darknet markets we looked at in our previous report still operate in 2023. While AlphaBay, a formerly major site that was shut down in 2017,2 has been resurrected, there are now 14 other completely new darknet markets where hacked account details are bought and sold. That number includes 4 Russian markets that sell this type of personal data. Another significant product offering on STYX are fake IDs and document forgery. With over 900 positive reviews listed on other cybercriminal websites and markets, “Podorozhnik” is one of the most credible vendors operating on STYX. His services are widely used by Dark Web actors to pass selfie and ID verifications required by digital banks, cryptocurrency platforms, and e-commerce systems.
While Google and other search engines index all of the websites on the surface web (also known as the clearnet) to make them easier to find, sites on the dark web are only found by word of mouth or links to them. Likewise, the term deep web also refers to sites on the internet that are not indexed and can’t be accessed via a search engine. However, deep web content includes any content that is behind a paywall or requires a user to sign in to access it. Surprisingly, U.S. payment card data costs around $6 and mobile phone numbers can be had for just $4.50 on average.



